tv National Governors Association CSPAN August 4, 2013 12:15pm-1:46pm EDT
12:15 pm
and you granted him a temporary reprieve -- four deaths and you granted him a temporary reprieve. why did you do that? guest: there can be no question that he had severe bipolar disability. there was no question that he wasn't guilty, and wasn't by reason of insanity. they got to eight or nine or 10 of the jurors and gave them this evidence that the kid clearly was severely bipolar. once they got him medications in 2005, he suddenly showed remorse and became a different person. when the jurors saw that information i said, that would've made a difference. three of them signed affidavits. at this point, it calls into question, this is not somebody
12:16 pm
who should be executed. want to look at all the facts around the issue, the part that struck me -- we spent $18 million or $19 million in all the appeals and legal issues, capital punishment trial until you get to the point of execution. that is not that different from many states. for life in prison without parole -- life in prison without parole as a couple of million dollars. dramatically cheaper. there is note n deterrent value o -- no deterrent value. texas celebrated their 500th execution. they don't have a lower level of homicides, no lower rate of mass murders. the states that got rid of the death penalty -- then the states that got rid of the death penalty. the families were split.
12:17 pm
some of the families desperately want to this perpetrator to be executed. but some of the other families, largely christian families that feel that the new testament in the bible is really about redemption and forgiveness, and if you execute this person it denies them the ability to keep working towards forgiveness. they really did not want an execution. that's not unusual. for not making all the family members of victims find closure, if it costs 10 times more money and is no deterrent, it makes you wonder why we are still having capital punishment. it begins to illuminate why there is no country in europe
12:18 pm
that still has capital punishment. outside of guatemala, there is no other country in this hemisphere that does capital punishment. australia, new zealand, israel have gotten rid of capital punishment. the real focus with this specific incidents was that the kid was clearly bipolar and refocus executing someone with that kind of a disability was not in the spirit of what was intended. host: and yet you pay the political price, at least in the polls. guest: sure. i paid a bigger political price for the gun safety issues and the universal background checks, which became very heated. when you have over 3000 people who are convicted or accused of violent crimes trying to buy guns and you stop them from getting guns, that is something you're going to support. whether it is capital punishment, universal background checks -- at some point, you just have to make sure you try to get people to hear the facts. when i go down the list of
12:19 pm
universal background checks and why we should expand it to all the gun purchases, republicans and democrats -- most of them say, i didn't know that. when i talk about how much money it costs for capital punishment and how there is no deterrence and it does not bring closure to the families of victims, people come back and say, that changes the way i think. host: john hickenlooper is joining us for mill walking, where the nga summer meeting is gathering -- from milwaukee, where the nga summer meeting is gathering. >> tomorrow, we will talk with michael harpster. he is with the fbi unit talking about child prostitution around the country.
12:20 pm
then tough insurance rates with kaiser health news and senior correspondent phil galloway -- galewitz. and we are heading now live to milwaukee for the final day of the national governors association meeting will be getting underway shortly. it is expected to start any moment now. the chair of this year's hearing l. governor markel the next session that they will be dealing with is the closing session, the state and cybersecurity. "the washington post" talks about why waiting for promised to fix cybersecurity is a waste of time by brian fung. it says that the commerce committee approved a version of the cybersecurity bill that now heads to the senate floor.
12:21 pm
12:23 pm
most significant vulnerabilities, leaving personal information, intellectual property, and critical infrastructure like in the electric grid all at risk from malware to spyware to distributed denial of services to phishing to intrusion to industrial insurance systems are growing in number and in sophistication.
12:24 pm
as we have heard from many different security experts, unless we really improve our countries cybersecurity infrastructure, the question is not if but when. -- not if but when there will be some major devastating coordinated cyber attack. some cyber attacks have been nuisances while others have been massive theft. while there have been significant levels at the federal level to protect the government domains, the role of the states and the role of governors have not been explored as much. the question is what action should we be taking to protect state-owned critical systems and how can states asked partner with the private sector, owner operators of google infrastructure, what are the
12:25 pm
theonents -- operators of infrastructure, what are the components and the risk landscape? these are just a few of the questions we have to consider. we have invited matt devoe, a national security expert who ,pecializes in cybersecurity counterterrorism, infrastructure protection, and intelligent with risk management district. he is probably the president and ceo of fusion xl c, which is a firm. cybersecurity he has been an adjunct professional at georgetown university since 2002. he teaches the flagship course, warfare and security. ask you to join me in welcoming him now. [applause]
12:26 pm
>> i'm going to bring my water because i just spent the last week at the black hat security conference in las vegas. so i'm suffering from a little bit of vegas voice here. i'm not here to talk about threats, although ice iceland on here -- although i threw this slide on here at to help you understand the activist organizations, you will obviously be missing the boat. the level of that view from the thread actors in cyberspace is grazer -- is greater than it seems on the course of the past 20 years. this is an initiative that have been working on. i was on one of the first cyber state responses at the national government level. what we see now in the private sector, the state-sponsored attacks are no less.
12:27 pm
you should be scared at this point. i will talk about putting that threat in context and some of the themes around managing cybersecurity. although we had a picture that i just showed you with all those different types of threats, you have to put that in context with regards to what threats will be targeting you can more specifically, what threats will be targeting what resources within your organization. so i will talk about those themes and themes of management and incident response and others. and thinking about what is your most likely attacker. if you think about it from a state perspective, is it a nationstate? is it an activist organization? is it an insider that is disgruntled? if we are going to put these issues in the context of risk management, which at the end of the day is what this is about, you have to spend some time thinking about what is your most likely attacker?
12:28 pm
even then, what is that attacker likely to target? one of the greatest issues i see is that we try to apply all threats to all problems. we try to say that all data is critical within an organization. and really, to manage this issue properly, we have to be beyond that and put it in a framework that we can understand and manage. the threat and impact, looking at the impact of the particular tech should also -- particular attacks also drive drive the resources. would be a cash traffic impact because it is targeting a prickle architecture -- a critical architecture? or is it an embarrassment to the organization based on data being released or sensitive information being released? do this without thinking about the impact of these attacks. the third kind of critical component is thinking about for -- thinking about vulnerabilities.
12:29 pm
the vulnerability impairment is something that needs to be managed with regards to what systems are in use, how they are used and what is the vulnerability profile. when we look at the attack to take place even with the most sophisticated the space best of the state-sponsored attacks, they don't have to bring their a game because we let them use their bnc teams. we need to do a better jobs in understanding those own abilities so we raise the bar and attackers are resource- constrained just like we are p.m. so we will increase the cost of the attacker and they can attack less good as a result, we get some inherent additional security. and make it about protecting the most important systems. one of the greatest mistakes we often see is that we will sit down with an organization and say what is important and they say everything is important. you can't manage an environment where everything is deemed as important. you have to make a decision. you have to govern this issue
12:30 pm
just as you would govern other types of issues. so if you sit down and say, we have the detects of data or types of system, howl of the -- how many of them fall in the bull's-eye of what is critical? and have you gone through the houses of identifying what these data sets are, what the systems are and then either critical or not? customers have had in excess of 50 different types of data. when you ask the individual players, they throw most everything in the bull's-eye. then towards the end of the cycle, when we have actually gone through the process, there might be three or four systems that are in that bull's-eye. levelafford the greatest of protection, the greatest level of monitoring. those are the systems that you're trying to protect from having a critical incident or having the data be released. at you have to go through the process to understand that. otherwise, your try to manage everything out of context. just to put it in a scene that might be a little more
12:31 pm
understandable, i chose this picture based on the security profile that we see here. because of the criticality of that position, we afford that level of protection. but -- but what if we try to do that for every member of congress or their staff? we would be resource constrained and we would be able to do it. it is the same thing in cyberspace. it is about making critical decisions and identifying those points that will be the highest threat, the highest impact are the most critical in the organization. unfortunately, the model right now and a lot of organizations as we try to do this with every single use of data and to make future to protect everything, you do not protect anything at all. examples include critical infrastructure. we hear a lot in the press about theft of intellectual property within an organization. that is a key issue. but even more so of concern to
12:32 pm
make him a based on my years of looking at these issues is critical infrastructure. being able to degrade infrastructure and all infrastructure and now, if it is critical, depends on computer systems and network for the operation of that infrastructure. i do not know of any infrastructure. -- i will welcome one if you have in your state, that does not have a network technology or bypass in some capacity. a blended threat where they can increase the impact of a conventional attack, like terrorism, by using a cyber attack in parallel with it. so making sure that critical communications will be there and the ability to respond. citizen and personal data is obvious a big issue and a high- profile one. because it attends to test it in -- it tends to attract a lot of headlines. it impact citizens at all
12:33 pm
levels. theou talk to them about critical infrastructure, they may not understand that, but if you talk to them about losing their social security number, then deficit in a personal context. and then financial transactions and data, we see all of the discussion in the pass from state-sponsored attacks and stealing intellectual property, but is much activity as there is in that environment, there is also criminal activity that takes place and there are actors were making hundreds of millions if not billions of dollars engaging in cyber crime. have financial transactions and financial resources that are available, those attackers will targeting -- will be targeting the systems as well. hasher key point that really emerged over the past several years or has been driven home by the recent attacks over the past three to five years, is that we have to shift away from a perimeter security mentality. we have been told for 20 years
12:34 pm
that security was about protecting the perimeter to put in a framework that we understood. to protect the persons in this room, we put yours on the outside good but the reality that come in cyberspace, perimeter security has been broken and will continue to be broken. so we have to inc. about side back -- cyber attackers being able us we have to think in terms of cyber attackers being able to get interior internal information. the key is what will be the impact of the successful breach and how do you manage that when that takes waste ca. the organization is at risk. if that puts the defense in context again of the critical data -- if i can have the curry motor-based mentality keep everybody on the outside, how do i protect the information on the internal network?
12:35 pm
what technology should i implement? they are looking for that silver bullet. there's no cyber cyber bullets in the space as well. there are enabling technologies that support increasing technology. but there is no one technology or a grouping of technologies that will solve this problem for you. it really is about management at a higher level. but there are these things i like to call sober concepts that can guide the discussion -- that i call silver concepts that can guide the discussion. ananizations don't have accurate technology of what operating systems they are running or what their vulnerability profilers. so there is a -- for file is. so there's a lot that they can do to raise their self awareness raise their security profile.
12:36 pm
pound for pound, especially against a lot of the attacks that we are seeing now am a spear fishing and the like, i think you get more value out of training and awareness programs than you do out of anything else. if employees make fewer sistakes, it introduces les risk into your environment. mitigation and management, not only of security in general, the mitigation of attacks as they take place, how do you respond? how do you measure your response? if you keep having attacks over and over again, how do you know you're getting better? threat intelligence and information sharing, we have gotten better at this. but the issue is that a lot of fact that a breach took place is treated as sensitive information and we are not sharing. that means we are also not sharing with the attackers did. the tactics, techniques and their procedures are not being
12:37 pm
shared. we have to be better at sharing that data because it helps enable all of the inert -- all of the organizations. i worked with 70 companies and see the attacks are taking place across all 70 companies. a best practices that are being put in place to mitigate those can serve as a conduit for sharing that information. any the same types of mechanisms as well among next -- amongst your organization's and with avid sector earners and with the federal government can training and awareness, we mentioned, again, pound for pound, raising awareness of what spearfishing was an e-mailis message that i received from a colleague at georgetown, a very famous counterterrorism expert, asking me for feedback on a particular project he was looking on -- working on. the problem was that the
12:38 pm
message didn't come from him. in the spreadsheet, if i had opened it, would have allowed an external attacker to take in the control of my computer. i didn't click on the attachment because i have a high level of awareness to be suspicious. bruce never mentioned this project to me. he usually does not interact with me over e-mail. it is usually in person or over the phone. so there were things that were interesting. when i hovered over the from and was coming address from, it was pretending to be his personal e-mail address at yahoo. but if i looked at my address book, it was one character offering his e-mail address. so they spoofed and did a good job. but there were several warning signs. you can train employees on these hangs. you can train them on how to particular confirmation and have better behavior associated with the use of technology. -- i throwg metrics this up as the metrics that we use with talking to boards of directors and ceos.
12:39 pm
i know a lot of you have private sector experience to recognize if i walk into a board of directors and say that there will file it is currently negligent. working you draw the line of to establishing best practices? a large majority never get to best practices. they want to have a diligent profile. they're putting the right programs in place, the right reduction strategies in place to have shown that they are exercising due care. it's about it -- it's about protection as well. you have to deal with incidents. we will always stop the bad guys and i any program in place for dealing with the consequences of a successful attack here in you have to have programs -- successful attack. you have to have programs to do the fact that that there will be breaches and deal with them. how efficient was your response? are you getting better at
12:40 pm
responding to attacks with fewer resources? are they having lessen impact and are they able to recover more quickly from an attack taking place? and thinking about it in the context of early detection and triage. when you have an attack, are you triaging the systems that have been targeted? anot of organizations from incident response perspective, there might be 10 systems that were treated all as equal. the reality is that one over here has a life-threatening illness or has a huge impact in your organization based on the attacker being successful. you have to focus your resources on those first. and containment, preventing the attacker from moving laterally within a network, preventing them from getting full access typical data. and then the intelligence sharing as a metric. what did i learn from this not only internally, but with pressure with others? and what can i take from others into my processes to make our response better?
12:41 pm
employee awareness metrics, getting employees to manage and report incidents. are you getting all of your incident reports from your i.t. staff because they detected on the network or are you getting employees saying, hey, my system is acting funny or i get the strange e-mail? attackedre going to be phishing, let's get it down to 40% next time. will attackers go after them? they see it before. and best practices, what sort of leak do you have out of your environments? what's are the data is being printed to perspective? -- are being put into perspective? the unfortunate reality is that coming responding to these these issues, we are playing lockable -- we are playing whack a mole.
12:42 pm
trying to find a program to capture this screenshot without getting my own personal computer infected with malware. is the desire to security model. you noticed that i did not put duct tape over all the holes. it is impossible to do that. but if i can do that over half of them come it makes the problem that much more manageable for me. that is a key thing we want to be doing. we want to be engaging in cyber risk management. problems need to be managed just like everything else. so we are really talking about an overall strategy for cyber management or cyber risk governance can what does that mean? you have to set up a strategy within your organization. you have to determine what your priorities are, unless you all have unlimited resources, which adopted is the case. you have to put in the context of what is the actual threat. having that awareness of who is targeting you or your peers,
12:43 pm
getting information from the government and putting it in that true context. having mitigation and ongoing processes for how you manage the devices that are in use in the organization, that are introduced into the. position and how you manage them on an ongoing basis. these attackers are successful sending their bnc teams after us because we do a poor job -- there be and see -- their b and after us because we do a poor job. training and awareness and response and recovery. , iwhen you do get breached guarantee you that you will get breached and you have some sort of plan that can contain and manage and reduce the impact of that incident. is of course, the challenge that you have to do it in the context of the resources they have available to you. that means you have to make choices and decisions. you want to make sure that you
12:44 pm
are making choices and decisions based on a framework and availability of data that puts things in the proper context. this is why they asked me to come to speak to and not just throw out slides to share ward souris -- war stories. really think about this as a problem that can be managed, they can be absolutely prevented, that you can put a management framework around and by the systems that are used in the state and the information that you have been entrusted with. that concludes my formal remarks. we have a couple of videos and then a q&a session. >> thank you very much. as many of you know, the nga center for us practices created the resource center on state cybersecurity. its mission is to help governors improve their cybersecurity posture by providing advice and some policy recommendations and resources that governors can adopt did interview the
12:45 pm
dissipated in the department of homeland security classified reefing on cyber security threats at our winter nga meeting. it is just one example what the resources center does. it is cochaired by two meters. .- by two cochairs they help provide an overview of the research center and the work underway in michigan and maryland can we have invited both governors to make a few comments. governor schneider could not join us in person, but he has videotaped some remarks. after that come i will ask governor o'malley to talk about what is going on in maryland. with that, if we could run governor schneider's via tape, that would be great. michigan governor rick snyder. as we move into the 21st century, the convenience of enhances our lives. at the same time, taxon are so the -- attacks on our safety continue to grow.
12:46 pm
we are committed to working with the nga and other states to enhance the cybersecurity prost year for everyone. orther it is identity theft those who prey on our children, these threat but sect -- these threats affect all of us. last year in michigan, we had 200 and 94 million spamware -- 294 million spamware. it's important that we are active. michigan is a leader in protecting this vulnerable ecosystem. agencies andnizing revamping site for training -- revamping cyber training programs. and through the michigan cyber range, which tests and improves capabilities, michigan is strengthening cybersecurity. in 2011, we launched with great success are cyber initiative.
12:47 pm
today, i'm glad to announce that come in october, we will host the 2013 michigan summit to continue this important work. we are committed to cybersecurity as we strive to take your families, protect their infrastructure, and she'll are economy -- and shield our economy. they give. -- thank you. >> with that, i will turn it over to governor o'malley. >> the presentation as follows. [laughter] honor knowngreat to want to thank you for your leadership on this front and for charging the staff to move forward on this. when most of us think about that imperative and security, we find ourselves between two different eras, one pre-9/11 in one post 9/11 and one of the eight new domains that has emerged in addition to air and land and sea and space is this domain of cybersecurity.
12:48 pm
that ire is a lesson think all of us have learned post 9/11, post katrina and other events. waiting for help to come from washington or even clear advice in these changing times to come from washington before we act is not a security strategy and it is irresponsible. we have seen most recently, i think, in south carolina, the damage that can be done by hackers and attackers. mr. chairman, in maryland, cybersecurity is a key component of our homeland security efforts and it is also an emerging sector of our innovation economy, creating lots of jobs in public and private sector as well. are the effective tool talents and skills of our people. it is eric greatest defense, our greatest offense. so we are investing in better programs in our schools, our high schools, our committee colleges khmer for-your universities, ensure that
12:49 pm
have the experience necessary to excel. , we created the maryland cybersecurity center at college park. and we've established the pathways to cybersecurity's careers consortium. we are raising awareness and educating our state employees through mandatory training, through cybersecurity drills and creating a regimen through our emergency management agency to make sure we do this on a regular basis moving forward. we are also working with businesses to develop employer- led training in this highly skilled high demand sector. that believe in our state the things they get measured other things to get done. i thought the presentation was outstanding. there are so many metrics in this area that we need to bring to the floor, create, and vocabulary, common language, common dashboards we have a sense of doing what we should and must to responsibly protect
12:50 pm
our critical infrastructure among which in this day and age, absolutely and positively has to include our cyber networks. our partnerships and collaboration are key. governor hickam who -- governor hickenlooper lexus it, cooperation is the new collaboration. experts from industry and academia are demonstrating that -- are demonstrating systems that are affordable and accessible. these men and women are outstanding. they have helped us in our exercises and drills and our training. i know that the council of governors is anxious to explore a better defined role for our national guard in this new domain.
12:51 pm
we also signed a $3 million cybersecurity tax credit into law to accelerate job growth in this field. for all of the focus that we have seen on the national level, we still have a lot of work to do in order to elevate the collaboration between a federal government and states in this realm. that is where the nga resource center on's eight cybersecurity's is working. we are working to fill the void. one of these tools is the governor's call to action for cybersecurity that will lay out a framework that all of us can pursue. governance authority, risk assessment, continuous vulnerability and threat assessments and the like. we also introduced an electronic dashboard that governors can use to understand their states level of readiness at a glance. moving forward, we are exploring for areas. we are looking for stronger collaboration between our states and our federal partners. second, looking for ways that the states can use their state-
12:52 pm
owned fusion centers to support stronger and more robust cybersecurity defenses on an interstate as well as an interstate basis. we are working to develop effective state policies to address the security of our data and our own infrastructure. fourth, we will be making recommendations on how governors can best develop a more highly skilled workforce of the needsanks that are out there in this new domain. so the work of the resource center is essential. we want to thank the able staff that has been working on this. thank you for your leadership on this. and also the grantmakers who have made this work au sable. the american gas association, cities deloitte, good technology, hewlett-packard, ibm, northrop grumman, semantic, and vmware. and i thank you again for the
12:53 pm
opportunity to bring everyone up to date. >> thank you. rick presentation. i understand that delaware and maryland are working together to sponsor and participate in the cyberspace is academy. we were one of the first states in delaware to host the cyber challenge can to attract young people to pursue a career in this area. we just graduated 47 students from our fourth annual camp. mentioned theley air guard and i think i see the tag of the wisconsin guard over there. ice to see you again. thank you for being here. let's all recognize the tag, please. [applause] thank you. they've been with us several times this weekend. we appreciate that. i was when to turn the conversation in that direction
12:54 pm
for a moment because heather from the nga health and homeland security information committee will give us an update. mentioned theley great work done in maryland and the incredible assets there to leverage something i've learned in delaware as well. heather, it's all yours. >> thank you. ,s governor o'malley mentioned in addition to the work of the cybersecurity research center, nga is working through the board of governors to address national cyber security vulnerabilities. a key focus of this work is looking at how the national guard can better be leveraged to meet the needs of both states and the federal government given its unique roles and response abilities. crowley, we know that all
12:55 pm
levels of government face a shortage of trained and qualified personnel to both protect cyber networks in advance and respond to intrusions and attacks when they occur. the citizen soldiers of the national guard announced there'd will roll so ring -- announced their role serving both governors and the president. this built-in talent can provide states and the federal government with access to leading-edge civilian declared skill sets that are not otherwise available within the government and some national guard units have taken the initiative to leverage the capability. for instance, in several states, the national guard is actively correlating with homeland security advisers and emergency managers to know cyber incident response plans did they are also -- response plans. they're also participating in exercises to deal with cyber
12:56 pm
incident responses. working through the council of governors, we are supporting efforts to expand and enhance an expert at the use of these kinds of capabilities. this will give governors and other to an the toolbox to address cyber security threats to at the same time, we are correlating with congressional offices to increase awareness of the guard as a readily available and cost-effective solution to the nation's cybersecurity challenges. bipartisan legislation was introduced this past spring in both the house and the senate to provide the guard a stronger role in cybersecurity and to provide each governor with a cyber incident response team. nga help support this legislation and help gain ingersoll support for their efforts. we have friendly seen a great deal of support in congress for these kinds of initiatives. but the house and the senate included -- in fact, required
12:57 pm
considering the national guard capabilities and what it can bring to the table. is council of governors, meeting again this afternoon to continue discussion on these issues. one of the primary goals of that meeting will be to encourage the federal government to actively partner with states to build and execute a conference a plan to address the nation's cyber capabilities. support continue to these and promote other efforts and opportunities for states to work in national level initiatives. thank you for the opportunity. i'm happy to answer any questions. >> thank you for the great job you're doing. what i would like to do is open it up to all of the governors, any questions either for our speaker or governor o'malley or for help -- or for heather or for anybody else.
12:58 pm
>> i wanted to follow-up on what heather was saying in terms of the guard. the cybersecurity center and the national guard just had an exercise. hackers --or at least ones who said they were. that is what we are doing right now is to set up our own cyber defense, if you will. we are doing wargames. we are trying to see what our vulnerabilities are. we call it a cyber range. combination of the guard
12:59 pm
capacity and the university point on our cyber defense spear. it -- it is an anti- computer access project. said, we do not have all of the results, but this can be done allegedly quickly using existing resources, is what i'm trying to drive at. the cyber capacity at the university, and the everyday training activity within the state department of defense, and the staffing there, is ongoing anyway. what we have done is formalized it. that is the principal forming our attempts to come to grips
1:00 pm
with some of the elements that have been cited so clearly here today. >> thank you, governor. anyone else? so, maybe i will ask heather again, because i think there is really interesting work going on across the country. i do appreciate governor o'malley sharing some of the details. is the most- what important thing that the governors can do now to take it to the next level with a resource that are available to them? >> excellent question. i think there's a real opportunity here. the key thing is to encourage the department of defense to move quickly and allow the national guard units that want to move forward in this area. u.s. cyber command is working on having the army and the air force, and the national guard workall of their resources
1:01 pm
on this issue concurrently. this session today, we have the good opportunity to drive that discussion forward. i think governor support for encouraging that to move as quickly as possible is going to be credible. just, just one further point? added, i made it sound a bit too optimistic. we just put this together. i would be interested in maybe to have -- an appropriate point will we are doing this with existing equipment. , part ofbeen donated the reason that we have been able to put this together that nobody wants the hardware that we're using right now.
1:02 pm
-- we areing to need going to lose on some of this, by the way. i do not bid we will be totally successful, because our defenses, if you will, are inferior. servers, inthe terms of the routers, etc.. enough toophisticated know all of it, but my point is that the equipment that we're -- we have top-notch people, but the equipment we are using is inferior. what is being told to me that we are going to have to make an investment if we want to go to toe than just being able retroactively defend ourselves. us deny those
1:03 pm
collaborations need to come on board. i would likeoint havederscore is that you great expertise. you know you need a governing structure for this, you know there are risk assessment that need to be conducted. you know that we need to do more training, and awareness of our employees. allhave the ability to do of those things combined also the ability to draw on your own financial services, to form your own cyber security council. you can say look, why are we waiting for washington in the inional guard, and everyone the federal arsenal to get a bus? -- to catch up with us? surecan i do now to make
1:04 pm
that we do not have a breach of personal information? >> that is really what i was try to get at. thank you. i have asked in delaware for that head of the department of technology education to see what steps we're are taking. it looks like a pretty good list and i am not sure what resources are available here for us at nga . i want to get the best in class set of standards. >> kenny rogers the dashboard, and some of the other questions -- can you run through the dashboard, and some of the other questions? there is a dashboard where there is a checklist, we are not talking about dreams and volumes of paper, we're talking about a simple sort of step and action you can take and go through. that is available through this center. and e-mails of our other partners who are part
1:05 pm
of this board. members who would be delighted to have a governor call them, or reach out to them, and save what advice can you give to me on this? as with the other homeland they needspects, drilling, training, and metrics laid out for us. >> who at nga is responsible for that? hei would ask thomas if could make sure that we all get that checklist that governor o'malley is talking about? areake sure, that as we questioning the people in our states that we are asking all of the right and tough, and appropriate questions. ok, thank you. with that, i want to thank all of you for this session. what i want to do now is to call
1:06 pm
the committee chairs, but i thank you very much for your recent additions. i want to hear it their brief reports of the work of the committee. national work on the resources committee, and the governor of south dakota. economicday, the development and congress committee, and the natural resources committee had a joint meeting. , it was ay productive session on the state of our nation's infrastructure. we had a couple of very good guest speakers. we first heard from the u.s. representative who is the chairman of the house committee for transportation and infrastructure. we got the vantage point of the house of representatives. immediately following his answers to questions, we
1:07 pm
received another distinguished guest, the newly up or did -- newly appointed secretary anthony foxx, who held forth on his blue points on our infrastructure -- viewpoint on our infrastructure. i want to thank everyone for being that meeting, and for participating in the discussion. >> thank you. >> for the education workforce committee, governor malloy. >> thank you. the education workforce ready, we discussed increasing workforce innovation to close the skills gap, create jobs, and grow family incomes. we had several distinguished speakers. governors discussed what we were doing our states in job creation
1:08 pm
at a, growth. we also discussed the reauthorization of the workforce investment act. , weimportance of restoring have 15% set-aside for our training programs that need to be put to local employers. remiss if we would be we do not take a moment to recognize the directive education and workforce committee who is working with us for more than a decade, and who ourmoved on to working with universities to make sure they are the best in the world. when she was hired, she was charged with putting governors back on the war front of national policy debates concerning education when there is no doubt that governors are on the forefront of those discussions. she has a desk in a fierce and effective advocate. i would like to ask you all to
1:09 pm
join me in applauding her service. [applause] that concludes my report. >> thank you. i want to add my word of thanks to joan as well. she has done a wonderful job. o'malley, on behalf of the halls and homeland security committee. >> mr. chairman, thank you. on friday, we met to discuss two important topics in both of them have to do with making sure that we are doing everything in our power to connect our veterans to employment opportunities. and other benefits when they come home for the battlefield, thewe were joined for presentation of alan hickey, the assistant secretary for the department of veterans affairs. they are making some important improvements there. they have been using modern technology to create, and clots wes -- robin platforms that
1:10 pm
can you stay wide to reach out to our active guard service, or army, our air force, or wherever they come from. fromso had presentations asretary of labor, as well the office of veteran services. the second half of that. the second half of that time we heard from the emergency management agency a dialogue on building and strengthening assets that we need to respond in the aftermath of natural disasters, whatever hits us. those were incredibly valuable, and we discussed coming out-of- the-box marathon, -- and we discussed the boston marathon bombing the vacations, insert
1:11 pm
capacity and the light -- like. i want to thank all of the governors who joined us. governorike to thank -- get -- mentioned governor walker earlier. once again, scott, thank you for doing such a great job. you want to make any closing comments before you take off? >> thank you. first of all, think you for coming to the milwaukee boy scouts, we appreciate it. i appreciate all of the governors, their families, their extended families, and all the others who came to our state. indulge me for a moment, i would to thank our commissioner of
1:12 pm
bureau who has done that. you saw a lot of the folks going in the turquoise shirts who were all volunteers from the community who helped of the last few days. i want to thank them. i also solved by the command center last night. we had a tremendous effort by the state control, the natural -- the wisconsin natural guard -- national guard. the milwaukee's county sheriff's office, our wonderful partners at the federal level, the fbi, the coast guard to buy with the thank all of them.
1:13 pm
governor markel, on a personal note, i want to tell you that not only your leadership of the past year, but also when i go through this session and every other one that you have held, your focus in employing people with disabilities has been inspiring. i have taken your document, and we are going to include it, we are going to carve out a segment for employing veterans. will also talk about the benefits of employing people with disabilities, and we will build off of that going into next year. we appreciate your leadership in , which has impacted each of us respectfully. ,o my friends, governor fallin who i have been a friend with even before we were elected. welcome to your new role in leadership. congratulations on being the
1:14 pm
interim vice chair. we joke about drinking beer, but i'm perfectly comfortable taking lite.inking coors on a more serious note, i want to wish all of you safe travels. most of you will fly out of the nearby airport, and i will be going just a few minutes south of that. year, a yearf last from tomorrow, we lost six lives . today we will be memorializing those six lives, and i would like to say i have appreciated all of you reaching out. very real sense, we will be celebrating the unity that i saw
1:15 pm
not just and the members of that temple, but the larger metropolitan community that came together and supported them. the shining example they have , the oldall of us adage that martin luther king jr. said, only love works. thatll be departing for edited little bit, but we appreciate you all being here today. would you please pass on to our -- your whole team our thanks for your great work. i would like to thank all of the governors for giving me the opportunity this last year for allowing me to serve as the chair for nga. all of thepreciate sport on building these initiatives.
1:16 pm
to washington, the bipartisan delegations, the work that you all have done with the nga committees and the like. many of the reporters who are here, are surprised how well we talk about politics in our meetings, and how much this is really about making policy, not democrats and republicans. i really appreciate the opportunity to work with all of the other governors. i also want to thank the nga staff who have done an excellent job. ony have them supporting me this initiative, and an absolutely first-class way. all of the staff who support our committees and the work that goes on in federal elections, the nga staff does doesn't and -- -- does an outstanding job. i would to thank you and your entire team for the great work
1:17 pm
that you do. [applause] yes, thank you. that, i do want to call governor malloy. unbelievably important session yesterday. governor malloy took the lead, along with governor christie. i just wanted very much thank you for that. i'm calling on you now as the chair of the nominating committee to give us the report of the next year's leaders for the nga. >> i would to thank you publicly for your great leadership and your commitment to finding employment opportunities for those with a disability. i've enjoyed working with you on that as well. on behalf of the 2013 dashboard -2014 nomination, i
1:18 pm
1:19 pm
well, thank you so much. governor markel, you have been an outstanding leader of the nga , and i very much enjoyed working with you on your initiative on employing those with his abilities and giving them a better tomorrow. you have certainly left your mark on our nation, you have certainly helped so many people around our nation vocus on the importance on helping those with disabilities be able to find jobs. encouraging us to work within our own state entities to put an emphasis on that zigler idea. -- particular idea. we have done several projects together already combined i know we will have a wonderful working relationship. we have a lot of good things we're going to work on in the future. governor markel, i would also want to say that we know when
1:20 pm
au aren't -- are in leadership position like this, it takes amount of time to do this job, but it also takes time from your staff. i want to say thank you to your staff. thank you to them for all that they have done. [applause] it has been a great pleasure for my staff to work with your staff. staff will become very close as we continue to move forward. thank you to your staff, and i know she is not here, but i also want to thank your wife, mark -- carla markel. she has been on a nice agenda for our spouses, which is important to help them feel engaged.
1:21 pm
we have some great programming, and some good bonding, so please express our thank you to your wonderful wife for all that she has done to help with this organization. sayso just want to something to one other person. appreciate much we our spouses because as i move into this position, i have to say thank you to my husband. he is here behind me. [applause] he is actually going to be taking over as the first spouse leadership council chair, so that is a new role for him. we're also joined by one of our six children that we have a tween us, and that is my daughter. [applause] always important to have your family present when you have a job like this. markel, ily, governor
1:22 pm
like to extend on behalf of our a gavel.vernors perhaps it is your final gavel, it is a symbol of art -- our appreciation, engraved to you. in commemoration of your leadership of the national governors association, to tell you how much we appreciate your leadership this past year. [applause] thank you so much. i'm very eager to begin this next year. we have a lot of work ahead of us. work is very important, and very valuable to our nation. we had a great week, thank you governor walker, and your team and your staff and all of the volunteers, all of the corporate sponsors. they made this convention possible.
1:23 pm
ofhad a great lineup speakers, topics, and a lot of fun activities. things this some ,eek, like riding a harley writing a coast guard boat, all of those things were fine. you had something great activities for us, we really appreciate you and your team for all the work that you do. as all of you know, each year the chair has the opportunity to select an initiative to work and focus on. proud to be able to announce my initiative. if i could ask the staff to begin passing this out. he is going to be called america works, education and training for tomorrow's jobs. [applause]
1:24 pm
i think that is something that certainly democrats and republican governors along with our orbit fellows and our private sector members are very attuned to and very engaged with. thisd so many discussions past week about the importance of our economy, our workforce education, and how we align all of those systems to be able to meet our individual state cost needs. needs.e's how to build a workforce that will meet the needs of america. economic regions have become more competitive, not only the united states around the world. i work first has become more specialized, and we have more specialized services, more specialized skills. public very garish resources that are available for workforce training. we have a lot of different
1:25 pm
workforce programs, so we need a thoughtful, comprehensive approach that will prepare the workforce to keep pace with a very competitive global economy. it is an issue that not only calls for national attention, but it also calls for editorial -- governor attention. way in helping to create a workforce in america that meets the demands that our need,ers in each state and also build a highly skilled workforce that we can reassure the jobs back to america. bring america back to its greatest. if you look at the statistics internationally, and where america stands and bears and many other nations -- in comparison to many other nations. -- in thethe area
1:26 pm
we are inading alone, the 20s. you look at math, we are 25th of the world. if you look at sign, we rank 17th out of 34 countries. ranking that low as a relation -- as a nation as great as we are, is unacceptable. we need to work together as governors to lead america back, to restore them back to the greatness of having the best educated, skilled workforce in our nation. require security will significant improvements in education and workforce programs. it will provide a pipeline to a better skilled, educated
1:27 pm
workforce we can meet tomorrow's jobs. it will also require a closer relationship,g and collaboration with our high schools, colleges, with our workforce training programs, our vocation training programs, and it will certainly require elaboration with our employers to make sure we know, as governors, what types of skills that our employers need. if you consider that nearly 50 years ago more than 75% of our jobs in america only required a high school degree or less to get a good wage. today, if you look at that number, it is -- has dropped to roughly 40%. fewer than one third of those jobs pay $25,000 a year. if your birthday, looking at it in another way, two thirds of
1:28 pm
the high school jobs available today will make less than $25,000. that is not due -- good for a national economy, that is not good for families, not good for children, not good for our future. parents generation, to have access to a good life, we know that today we have to have an educated workforce that has mainly an associates degree, or a college degree, or some type of workforce training certificate to be able to meet the minimum required for jobs today, and jobs of the future. we need to do a better job of providing for all of our students the opportunity to successfully be able to navigate through our education system. to make sure that they are
1:29 pm
entering into a pipeline with some type of either education beyond high school, or into a pipeline with a career technology field. there are too many students that over their own potential by limiting access to resources. ago, the nga launched a major initiative, and it was to have more degree completion within a workforce, within our high schools, without our colleges, with an art career technology programs. we call the complete college america, and it was implemented in the majority of our state. it was a challenge for us to get more degree completion into the pipeline of our workforce. nationally, we know that just more than three quarters of our public high school students will make it to graduation. if three quarters of them make
1:30 pm
it to graduation, we know that those that continue on to post , we know education that only half of them will finish that education. that makes us fall behind as a nation when you look at those international graphics of where we fall. the math, science, really feel that we have. americans of the workforce is now working age they lack the basic literacy skills, and also struggle with numbers. that does not help when coming to qualify for the jobs we have available today. the challenge as governors we have is very clear. we need to get more students into higher academic standards, within our high school systems, graduation help them
1:31 pm
-- readily for my school. we need to help them further their education, to go on to an associates degree, a four-year college degree, or even beyond. or, getting a workforce career certificate, so they can have a career path of some sort. i would help us have a more sustainable, stronger, national economic security for our nation. introduced, we also -- also have to do several things for the challenge. we also need to lay out a pathway, a roadmap if you will, on how to achieve a higher economy with a stronger, more highly educated workforce. goodob is to develop a place of smarter data. we know where our workforce falls within each of our state. that way we can better understand what is needed by our
1:32 pm
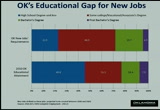
employers, our industries, our associations. we will work with the private sectors. we also work more with our state governments, to build collaboration between industry and business, and our indication -- education pipelines. we are also going to work on improving the quality and expanding pacitti of the education training institutions that prepare our workforce. we are going to encourage innovative partnerships among our business communities, our education institutions, and our government. there are some great examples across our state. let me just make this initiative a little more tangible to you. this is just oklahoma alone on this slide, and we're going to get each of your states this type of analysis. if you do not know where you are, we cannot get there.
1:33 pm
we are going to give you that roadmap. if you look at this chart, you're looking at data on if youa's workforce and start with the bottom graph, it shows that oklahoma's current education level with a percentage of those with high about 45%.omas is shows that 31% of oklahoma's workforce has spent time in college, or has an associate degree rate the green bar shows about 15% of obamas workforce has a bachelors degree, or above that. the purple shows they have a doctorate or master degree.
1:34 pm
if you compare that to the chart up above, you'll see that the top bar shows the percentage breakdown at the degrees level required for the jobs that will bycreated in our state looking at the various industries and skills that meeting. the degree that will be needed, and the workforces that will be needed in the years 2010 to 2020. the blue bar, as you can see, we have a pretty big gap in our skill set. jobs will bef required for high school compared to those that will be for those with a college degree, is about 22%. there is a mismatch in the degree to which we are educating our young people, and educational needs that will be demanded as we help move them into jobs to grow our economy. greek --ee the higher
1:35 pm
degree education level, the percentage they will be needed in the job force. in simplest terms, what we are hoping to do with this initiative is to help be able to generate the level of data that will be our net, that will be that will help as they again to edify specific strategies were each of their states. to begin to align those results between b and education itself, and the needs of the emerging workforce. as we begin this initiative, we want to make it really clear that the role of education must be more than just to prepare our individuals and to have some wantof degree, but we also to collaborate with the private sector. -- maketo make that our
1:36 pm
sure that our students and working adults have the type of skills that will be needed to my that will be ardent towards the type of jobs that will be created. we also need to understand that post secondary degrees and workforce certificates are now the new minimum for our nation. things have changed since our parents. it, if we do not set these new standards, we do not work on these pipelines for prosperity, our young adults will be facing many different hurdles as they try to ring into the middle class. as they try to chase the american dream. it will also limit our ability as a nation to be able to become stronger, to become more vibrant, and move the economy forward. just recap, america works, education and training for tomorrow's jobs will focus on engaging our education about our
1:37 pm
businesses, our government leaders, and what we can do as governors to be able to work 12re closely with our k- education systems, our colleges, i workforce training programs, to meet job demand. we will work with the governors to prepare this data for each of your states, to talk about shoretel labor -- to talk about your labor demand. to meet thesel demands, and then we will take able to maketo be sure we have the type of result that we desire. i think there is nothing more critical than securing the economic future of america, and also being able to prepare our workforce for the 21st century jobs. that is something that we are
1:38 pm
looking forward to working with each of the governors on. anduldn't think the staff, -- i want to thank the staff, , and our director of education. all you thank you for hadn't -- and your team have done to put this together. we will be scheduling summits across the nation. we will be able to bring forth the data that we are compiling for each state. it will be up to each governor to decide how they want to implement that data. how will work with your education pipelines, and workforce training programs. i think it is something that is very critical if we're going to continue to build a stronger, more vibrant economy. as we all talked about, bring those jobs back to america, keep them in america, and make sure that our children have the best future possible.
1:39 pm
1:42 pm
>> wrapping up the final session of this summer's nga session on cybersecurity. year'sir for next session is oklahoma governor, mary fallin. for this cybersecurity discussion, congress and the president involved in cybersecurity, and that will moving onto the senate. we will take your calls momentarily. role inout your state's cybersecurity. and if you're joining us by those numbers are --
1:44 pm
>> we are watching governors and they'll wrap up the final session at the nga. the topic was cybersecurity. the question that we are posing to you, what is your state's role in cybersecurity? our first call coming from cloverdale, indiana. i think my state's role as far as the governors meeting their is just to cooperate with the federal agencies him and the
1:45 pm
federal government. guidance ash their i think the federal government is the best way to spread whatever needs to be spread down as far cybersecurity. >> what did you think of what the governors had to say here? do you think they would go along with taking the federal lead? >> i would hope so. i would hope that they would not play partisan politics. i hope their constituents would not override what the government has to say. i just think the thing to follow the federal government instructions. >> thank you. i just want to know
78 Views
IN COLLECTIONS
CSPAN Television Archive
Television Archive  Television Archive News Search Service
Television Archive News Search Service 
Uploaded by TV Archive on

 Live Music Archive
Live Music Archive Librivox Free Audio
Librivox Free Audio Metropolitan Museum
Metropolitan Museum Cleveland Museum of Art
Cleveland Museum of Art Internet Arcade
Internet Arcade Console Living Room
Console Living Room Books to Borrow
Books to Borrow Open Library
Open Library TV News
TV News Understanding 9/11
Understanding 9/11